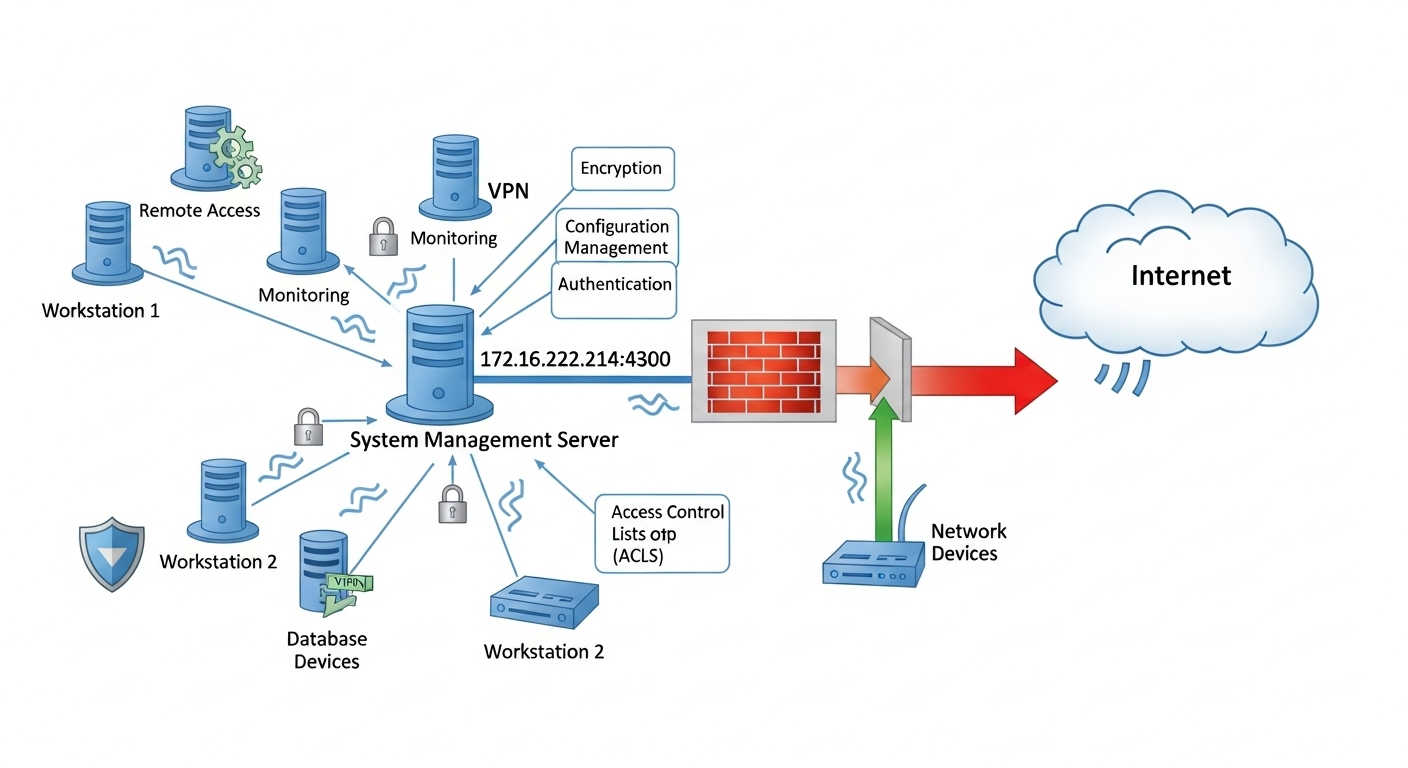
In the ever-expanding world of networking, certain numbers and addresses might seem random, yet they hold deep significance for IT professionals and tech enthusiasts. One such mysterious address is 172.16.252.214:4300. If you’ve stumbled upon it, you might be wondering what it represents, why it appears in network configurations, and whether it’s safe or risky. This article dives into the fascinating world of IP addresses and ports to explain 172.16.252.214:4300 in a simple, human-friendly way.
Understanding the Basics of 172.16.252.214:4300
To begin, let’s break down 172.16.252.214:4300 into two main components: the IP address and the port number. The first part, 172.16.252.214, is an IPv4 address, while :4300 is a port number attached to it. Together, they create a unique identifier for a device or service on a network.
The IP address 172.16.252.214 falls under the “private IP range” according to Internet standards (RFC 1918). This means it is not routable on the public internet and is usually found inside local networks such as offices, schools, or home setups. When combined with the port 4300, 172.16.252.214:4300 typically refers to a specific application, service, or internal server operating within that local environment.
The Role of Private IPs like 172.16.252.214
Private IP addresses, including 172.16.252.214, exist to help conserve public IPs and secure internal networks. Instead of assigning every device on your Wi-Fi a public IP, routers use private IPs like 172.16.252.214 for communication within your home or company network.
When a device connects to the internet, it uses a process called Network Address Translation (NAT). NAT converts the private address, like 172.16.252.214:4300, into a public one so that it can communicate with external servers. Without private IPs, network organization and security would be much harder to maintain.

What Does the Port 4300 Represent?
The port number in 172.16.252.214:4300 identifies a specific service or process running on that IP address. Ports act like doorways through which data moves in and out of a system. The number 4300 isn’t assigned to a standard internet service like HTTP (port 80) or HTTPS (port 443). Instead, it’s typically used for custom applications or internal tools.
For example, in a business setting, 172.16.252.214:4300 might point to an internal web service, database, or custom-built application used by employees. Developers often choose such port numbers to avoid conflicts with widely used ports, giving them flexibility and enhanced control.
Why You Might See 172.16.252.214:4300
There are several scenarios where 172.16.252.214:4300 may appear:
- Internal Testing – Developers and IT engineers may use 172.16.252.214:4300 to host a test server or application within a company network.
- Local Applications – A software program on your computer might communicate with a local service running on 172.16.252.214:4300.
- Configuration Files – Sometimes, network configuration files or logs reference 172.16.252.214:4300 to track activity or connection attempts.
- Network Scans – If you perform a scan to identify open ports in your network, 172.16.252.214:4300 might show up as an active endpoint.
Each of these cases is normal within private networks, but it’s essential to verify the purpose of any service running on that address to ensure it’s legitimate.
Is 172.16.252.214:4300 Safe?
The safety of 172.16.252.214:4300 depends entirely on what’s hosted at that address. Because it’s a private IP, it doesn’t pose a direct threat to internet users. However, within a local network, misconfigured or vulnerable services running on 172.16.252.214:4300 could be exploited if not properly secured.
To ensure safety, network administrators should:
- Regularly scan for open ports like 172.16.252.214:4300 to identify unauthorized services.
- Use firewalls and access control lists (ACLs) to restrict access.
- Keep all software and operating systems up to date to patch vulnerabilities.
- Monitor network traffic logs for unusual patterns related to 172.16.252.214:4300.
By taking these precautions, the network remains secure while still allowing essential internal services to function.
Common Misunderstandings About 172.16.252.214:4300
Many people mistakenly think that 172.16.252.214:4300 is a public or dangerous IP address. In reality, it’s part of a trusted range of local addresses. Unlike suspicious IPs found online, 172.16.252.214:4300 cannot be accessed from outside your network unless your router’s NAT settings expose it — which is rare and generally discouraged.
It’s also worth noting that just because you see 172.16.252.214:4300 in a log or error message doesn’t automatically mean something is wrong. Often, it simply indicates a temporary local connection between devices or services within the same network.
Troubleshooting 172.16.252.214:4300
If you encounter connection errors involving 172.16.252.214:4300, here are a few quick troubleshooting steps:
- Ping the IP address to confirm whether it’s active.
- Check your firewall settings to ensure port 4300 is open if the service requires it.
- Verify application configuration — the service you’re using may expect a different IP or port.
- Consult network logs to trace recent connections to 172.16.252.214:4300.
By methodically checking these factors, most network issues tied to 172.16.252.214:4300 can be easily resolved.
Practical Applications of 172.16.252.214:4300
Tech professionals often utilize 172.16.252.214:4300 for:
- Hosting local APIs for in-house development.
- Testing server deployments before pushing them live.
- Running sandbox environments for secure experimentation.
- Facilitating communication between microservices in a distributed system.
Because 172.16.252.214:4300 operates within a private scope, it’s ideal for experimentation without risking exposure to the public internet.
Final Thoughts on 172.16.252.214:4300
In conclusion, 172.16.252.214:4300 is more than just a random sequence of numbers — it represents a private communication channel that plays a vital role in modern networking. Whether used for development, testing, or local services, it symbolizes the invisible structure that keeps networks secure and organized.
Understanding how 172.16.252.214:4300 works helps demystify how internal systems operate, offering insight into the core of network management. Next time you see 172.16.252.214:4300, you’ll know that it’s not a threat, but a key part of the infrastructure that makes digital communication possible.